Price: 5.00 USD | Size: 4.04 GB | Duration : 4.42 Hours |51 Video Lessons | ★★★★★ 4.5
BRAND : Expert TRAINING | ENGLISH | INSTANT DOWNLOAD
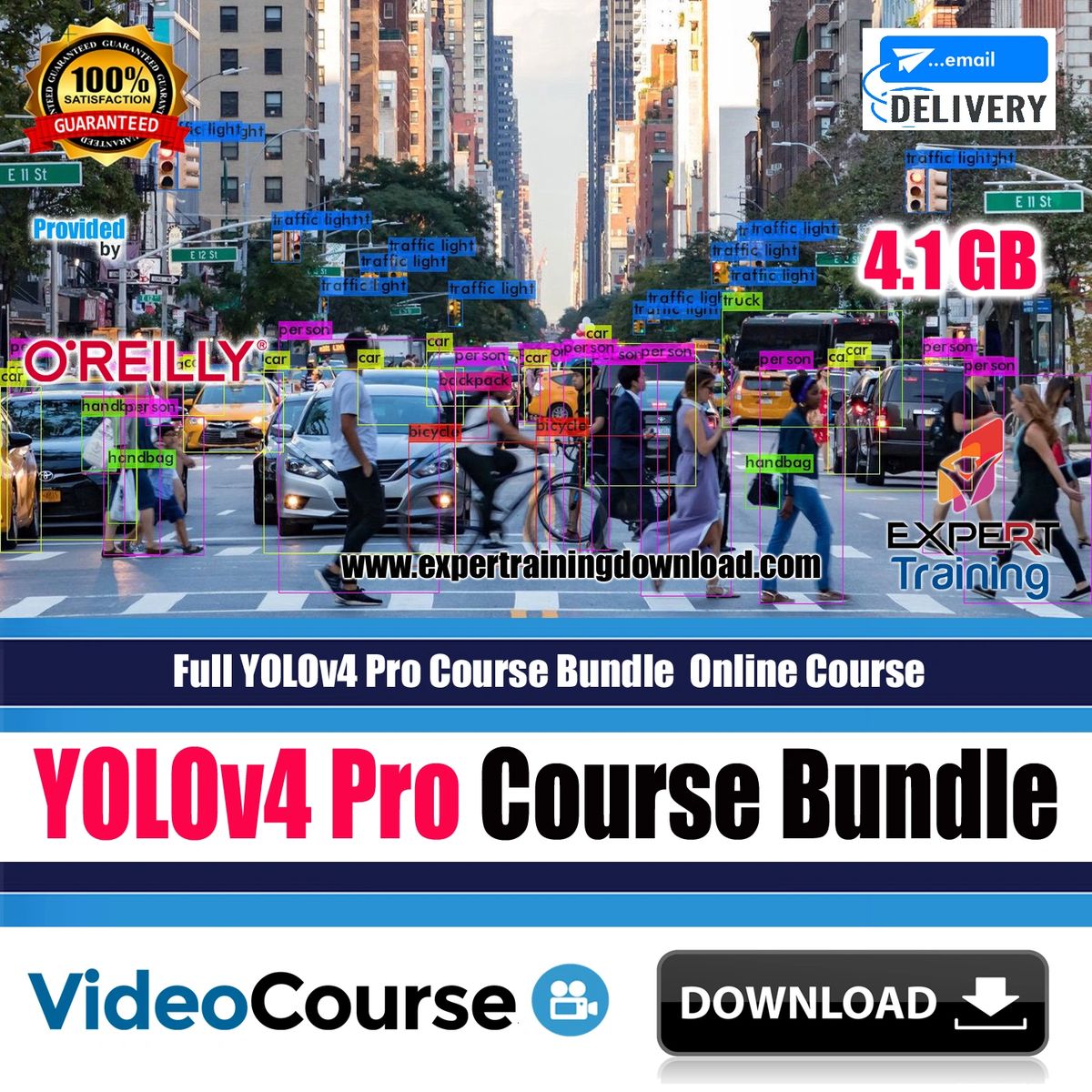
Full YOLOv4 Pro Online Course Bundle
Video description
Learn how you can implement and train your own custom YOLOv4 object detection models in computer vision
About This Video
Social distancing app to calculate the distance between people to determine if they are at risk
Object counting app for counting cars in a parking lot and DeepSORT to track vehicles in traffic
Mask detection app to detect whether or not a person is wearing a mask; if not, flagging an alert
In Detail
This course is a perfect fit if you want to natively train your own YOLOv4 neural network. You’ll start off with a gentle introduction to the world of computer vision with YOLOv4, install darknet, and build libraries for YOLOv4 to implement YOLOv4 on images and videos in real-time.
You’ll even solve current and relevant real-world problems by building your own social distancing monitoring app and implementing vehicle tracking using the robust DeepSORT algorithm.
After that, you’ll learn more techniques and best practices/rules of how to take your Python implementations and develop GUIs for your YOLOv4 apps using PyQT.
Then, you’ll be labeling your own dataset from scratch, converting standard datasets into YOLOv4 format, amplifying your dataset 10x, and employing data augmentation to significantly increase the diversity of available data for training models, without collecting new data.
Table of contents
Chapter 1 : Introduction to the Course
Introduction
How to Excel in this Course
YOLOv4 Theory
Installation of YOLOv4 Dependencies such as CUDA, Python, OpenCV
Chapter 2 : Object Detection with YOLOv4
YOLOv4 Object Detection on Image and Video
YOLOv4 Darknet Explanation with Code and Webcam Implementation
Social Distancing Monitoring App
Social Distancing Monitoring Coaching Session
Count Parked Cars
DeepSORT Intuition - How DeepSORT Object Tracking Works
Robust Tracking with YOLOv4 and DeepSORT
Chapter 3 : YOLOv4 Starter Summary
Evolution of YOLOv1 to YOLOv3
YOLOv5 Chess Piece Detection
Bernie Sanders Detector
Chapter 4 : Labelling a New Dataset in YOLOv4 Format
Introduction to Data Annotation
YOLOv4 Format for Image Labelling
YOLOv4 Labelling Tools
Web-Scaping Data
Annotating Images with LabelImg
Labelling on Video Using LabelImg
Labelling on Video Using Darklabel
Label Objects on this Video
Annotation Summary
Data Annotation Key Takeaway
Chapter 5 : Creating Custom Dataset in YOLOv4 Format
Introduction: How to Create Custom Dataset
Toolkit for Downloading Image Datasets
Downloading Images from Specific Classes
Converting Downloaded Files to YOLOv4 format
Data Augmentation Using Rotational Transform
Summary - Key Takeaways for Custom Datasets
Chapter 6 : Training YOLOv4 Using Darknet Framework
Introduction to Training YOLOV4 with Darknet Framework
Step 1 - Configuring the Files for Training
Step 2 - Creating the obj.names File
Step 3 - Dataset Placement for Training
Step 4 - Train Test Metafiles
Step 5 - Training YOLOv4
Trained YOLOv4 Execution on Image and Video for Mask Detection
Activity: Train on Your Own Dataset
When to Stop Training
Summary - Key Takeaways
Chapter 7 : PyQT User Interface for Object Detection with YOLOv4
Introduction to Object Detection with PyQt
Installing PyQt
GUI Layout Using PyQt Designer
Integrating PyQt with YOLOv4
Code Explanation
Adding GUI Widgets - Counting Objects
Adding Widgets - Slider Threshold
Adding Widgets - Class Filter Using Checkbox Widget
Adding Widgets - Real-Time Live Plot Graph Widget
Social Distancing in PyQt Activity
Conclusion
Finally, you’ll develop your own Mask Detection app to detect whether a person is wearing their mask and to flag an alert.
By the end of this course, you’d be able to implement and train your own custom CNNs with YOLOv4. It will help you in solving real-world problems, freelancing AI projects, getting that opportunity in AI, and tackling your research work by saving time and money. The world is your oyster; just start exploring the world once you have skills in AI.
Who this book is for
This course is for developers, researchers, and students who have at least some programming experience and want to become proficient in AI for computer vision and visual recognition. An individual with machine learning knowledge and who wants to break into neural networks or AI for visual understanding, a scientist looking to apply deep learning + computer vision algorithms, individuals looking to utilize computer vision algorithms in their own projects will highly benefit from this course.
A high-range PC/laptop, Windows 10, and CUDA Nvidia GPU graphics card are pre-requisites.
Table of contents
Chapter 1 : Introduction to the Course
Introduction
How to Excel in this Course
YOLOv4 Theory
Installation of YOLOv4 Dependencies such as CUDA, Python, OpenCV
Chapter 2 : Object Detection with YOLOv4
YOLOv4 Object Detection on Image and Video
YOLOv4 Darknet Explanation with Code and Webcam Implementation
Social Distancing Monitoring App
Social Distancing Monitoring Coaching Session
Count Parked Cars
DeepSORT Intuition - How DeepSORT Object Tracking Works
Robust Tracking with YOLOv4 and DeepSORT
Chapter 3 : YOLOv4 Starter Summary
Evolution of YOLOv1 to YOLOv3
YOLOv5 Chess Piece Detection
Bernie Sanders Detector
Chapter 4 : Labelling a New Dataset in YOLOv4 Format
Introduction to Data Annotation
YOLOv4 Format for Image Labelling
YOLOv4 Labelling Tools
Web-Scaping Data
Annotating Images with LabelImg
Labelling on Video Using LabelImg
Labelling on Video Using Darklabel
Label Objects on this Video
Annotation Summary
Data Annotation Key Takeaway
Chapter 5 : Creating Custom Dataset in YOLOv4 Format
Introduction: How to Create Custom Dataset
Toolkit for Downloading Image Datasets
Downloading Images from Specific Classes
Converting Downloaded Files to YOLOv4 format
Data Augmentation Using Rotational Transform
Summary - Key Takeaways for Custom Datasets
Chapter 6 : Training YOLOv4 Using Darknet Framework
Introduction to Training YOLOV4 with Darknet Framework
Step 1 - Configuring the Files for Training
Step 2 - Creating the obj.names File
Step 3 - Dataset Placement for Training
Step 4 - Train Test Metafiles
Step 5 - Training YOLOv4
Trained YOLOv4 Execution on Image and Video for Mask Detection
Activity: Train on Your Own Dataset
When to Stop Training
Summary - Key Takeaways
Chapter 7 : PyQT User Interface for Object Detection with YOLOv4
Introduction to Object Detection with PyQt
Installing PyQt
GUI Layout Using PyQt Designer
Integrating PyQt with YOLOv4
Code Explanation
Adding GUI Widgets - Counting Objects
Adding Widgets - Slider Threshold
Adding Widgets - Class Filter Using Checkbox Widget
Adding Widgets - Real-Time Live Plot Graph Widget
Social Distancing in PyQt Activity
Conclusion
Related to:
yolov4
yolov4 classes list
training yolov3 for object detection with custom data udemy free download
best object detection course
yolov4 tutorial
yolov4 ros
yolo object detection course
yolov4 download


Comments
Post a Comment